Why this sector?
Simple; it’s literally where the money is.
It’s objectively a tumultuous time in history. With new paradigms being introduced to the banking and finance industry in the form of cryptocurrency and blockchain, AI/ML, and the ubiquity of digital adoption by consumers, it’s no surprise that there’s a spike in cyber threats.
“Targets in a state of flux are always softer.” – Gordon Draper, CEO of Fort Safe
Because it contains vast amounts of accumulated wealth and with many (and rapidly moving) parts to the machine, there are new gaps. New opportunities for compromise.
Unique Threats and Vectors of Attack to Financial Institutions
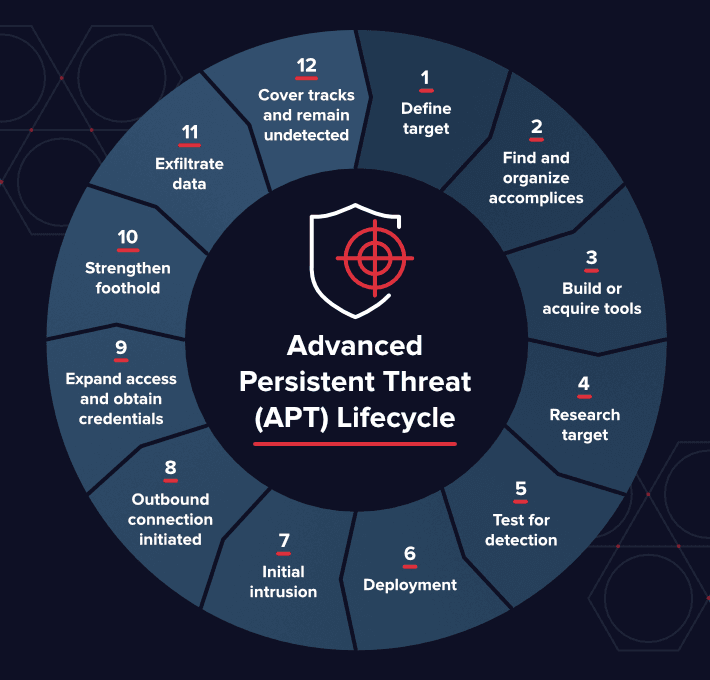
The huge fiscal potential of attacks in banking and finance compared to say, the retail industry, means huge potential windfalls translating to greater investment by criminals. Over the past decade we’ve seen the mirroring of corporate entities within cyber criminal organisations. There are fully fitted offices, boards of directors, proper PnL reporting, and of course, the worker bees responsible for technical execution. They are sometimes funded by state-actors giving them resources (or at least the latitude) to go about their business with impunity. This level of ‘professionalisation’ means that Advance Persistent Threats (APT’s) are incredibly focused, and seemingly with a steady eye on banking and finance.
Even 20 years ago, transferring money between banks was a relatively low-volume affair. With the advent of the internet and the birth of a truly globalised economy, the interplay between institutions has skyrocketed. Since the first (recognisably modern) incarnation of SWIFT in the early 2000’s, financial institutions have roughly 10x’d their daily rates of messaging to over 25 million.
The rapid adoption of SWIFT gpi (a private blockchain) to a level where over half of international transfers since 2017 provides some indication as to the precipitous rate of change the industry is experiencing. While initiatives like SWIFT gpi are assuredly advantageous, there is a knock-on effect; required patchworking or hastily instituted measures replacing archaic pre (or early) digital technologies in the wake of these more testable changes to meet the adoption of new tech. A concurrent rise in the total volume of traffic across all core systems like SWIFT which alone has seen a trending >10% YoY providing a total of 56% growth obviously increases the appeal as a target of attacks. And there’s the rub. A new, powerful technology creates new vectors, widening the possible attack surfaces as tech is rolled out, and at the interface with erstwhile ‘secure’ legacy systems.

A prime examples of this ‘weakest link’ scenario is the SWIFT hack of the central Bangladesh Bank. Many of the critical factors of the equation were adequate; SWIFT AA was current as was the Oracle DB involved. But there were critical gaps in their overall approach – like the use of consumer-level switching equipment – that allowed these to be compromised.
Unique tool combos; Trickbot and/or Emotet earlier in 2018 were the go-to trojans for banking and finance. The ability to iterate incredibly rapidly gave rise to polymorphic phishing as the flavour of the day, and avoided most typical heuristic matching. Even when targeting general corporate entities with whaling (where senior executives are phishing with highly personalised attacks) success rates were high – in fact, higher than the general populous open rate, according to The Email Laundry.
The Acceleration of Change
Fintech is booming, more so than most other industries. The start-up landscape is littered with the stellar debris of cryptocurrency rising stars of 2017/18 that have collapsed in on themselves. What this period demonstrated though, is that innovation is on a hair-trigger when opportunity presents itself to the market. Support from governments for general fintech innovation is happening, albeit lagging somewhat. Many start-ups that entered during this time when blockchain was cryptocurrency. The perception of value in blockchain has changed, and many fintech start-ups are now using blockchain as the basis or an addendum for their projects. Whether marketplace/exchange creation, lending apps, or business payments new tech and new platforms are causing quite the stir in a traditionally stable industry. This influx of new ideas and the growing appetite institutions are showing toward using these platforms to win over consumers, is creating new vectors. Smaller private blockchains are more likely to be compromised through ‘selective endorsement’ insider attacks. While much of this is tea-leaf speculation, the blind enthusiasm to migrate distributed databases to blockchain solutions is fraught with potential peril. It will be interesting to what happens

An Oldie But a Goodie
Adoption of new fintech provides new footholds for cybercrime in any industry. As with the SWIFT cases earlier, the integration of new technologies can prove damaging. But the more industry agnostic threats are certainly still relevant.
All industries are seeing an increase in mobile cybercrime, mirroring user adoption as a platform of preference. Related to the changing face of banking, the consumerisation of interfaces means that even the UX for business banking is going mobile too. While convenient, the relative infancy for mobile security means that we will see a growing interest in mobile platforms for cybercrime, and this industry is certainly not an exception.
While every organisation with employees runs the risk of insider threats, banking and finance has a substantial risk associated with its operations. Tools are evolving to deal with these threats – particularly AI identifying anomalous behaviour – but most attacks we’ve seen in recent history from the Bangladesh Bank, the Pakistani spate of attacks at the end of 2018, all allegedly involved some angle of insider threat.
Unencrypted data, while less of a problem in Australia than other parts of the world, can still cause complications in modern economies. Things are evolving, however slowly, but the burden of legacy systems can’t be unshouldered so soon.
Positive Signs
Growing interest and a sense of urgency from governments in compliance measures can be seen both globally and domestically. This has the knock-on effect of businesses budgetary commitments to security. When the risks keep increasing, and just as importantly, the reporting of the risks keeps increasing, organisations take notice and are more proactive in their approach. While security can’t be solved with simply more resources are always welcome. They just need to be put to intelligent, judicious use.
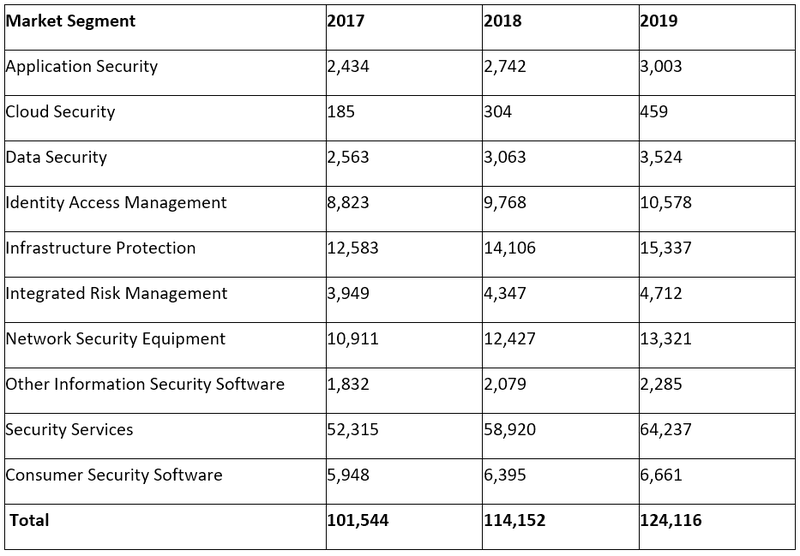
Worldwide Security Spending by Segment, 2017-2019 (Millions of U.S. Dollars)**
With the usual ebb and flow of ITO/MSSP’s (IT Outsourcing and Managed Security Service Providers) and back to internals, organisations run the risk of slotting into essentially a single-provider solution. Then it becomes a question of, “Who polices the police?”. That’s where we’re seeing a growing appreciation for niche specialists like Fort Safe for finance sector. With nuanced understanding, these specialists can bring fresh perspective to audit functions like penetration tests for the banking and finance industry.
Low-hanging Fruit for Prevention
The CEO of Fort Safe, Gordon Draper, recommends the following essential steps to improve the security posture for your finance organisation;
- Two factor authentication on everything that is high assurance (medium confidentiality, high integrity, high availability) (financial services apps, business email, Any Software as a Service, Admin panels on websites). Don’t use SMS for 2FA. Use biometrics or Timed One Time Pass code (Google authenticator)
- Password manager using at least 16 character strong random passwords (such as Last pass, 1password etc)
- Phishing Awareness training (email, voice, text)
- Laptop Encryption – Microsoft Bitlocker or similar products
- Mobile phone protected by biometrics or long pass code and encrypted storage.
As an addendum, when it comes to engaging external firms, requesting a pentest of your software environments should be the focus over other testing.
Many financial institutions will insist on 2FA for all transactions, and the challenge will become limiting the adoption-friction for users.
Banking and Finance Industry Predictions – 2019
Increases in sophisticated phishing attacks. With the advent of banks chasing consumers, they are beginning to offer multiple channels for interaction including chatbots, AR, and rapid adoption of voice platforms like Amazon’s Alexa, more vectors will emerge to take advantage of these largely untried endeavours. As a somewhat related topic, the rise of ML in the industry for the ingest of vast amounts of records (particularly with M&A) may see this as a possible route for several types of injection.
While ransomware will remain prominent, it will likely continue to plateau, the flattening even more pronounced in finance. With some of the volatility coming off the cryptomarkets, crypto is now being seen as more of a stock commodity rather than the gold-rush effect we saw in at the tail end of 2017. This counterintuitively sees it becoming a more valuable commodity as the risk ascribed is blunted by the loss of its celebrity. Hence, we are seeing a move away from the ‘your money or your life’ approach of ransomware, toward a less direct and antagonistic cryptojacking. It’s a mosquito, not an alligator. Though with enough of a swarm…

There will be a global rise in GDPRization. While the enforcement aspects and formal legalities will be trailing the lead, we’ve seen many new laws being bandied about in 2018 with many people unsure of where things will fall. I believe some of the proposed measures will be adopted either federally like 2015’s Consumer Privacy Bill of Rights Act (CPBORA) or by key states like California’s recent CDPA and depending on the appetite for Marco Rubio’s American Data Dissemination (ADD) derisory proposal. Regardless of outcome, these efforts are a good barometer for governments growing interest in the face of the publics increasing expectations to privacy. Regionally, Australia has already established mandatory data breach notifications, and we’ll see more of these making news in 2019. The thing post-election, will be how the intersection between Open Banking initiatives and Consumer Data Right (CDR) will play out. The Australian Banking Association (ABA) has already stated that the Treasury is woefully unrealistic in its threat assessments, and I tend to agree. This tabled policy will have to evolve to meet the shifting of attacks on banking and finance institutions, particularly in terms of perceived levels of risk in credential compromise. Regardless of agreements, timelines for adoption will most assuredly blowout considerably given the high-risk nature of this endeavour and we’ll be lucky if we make the 2020 timeline for many of the elements.