Personal Information, what’s the Big Deal?
In the Digital Age, personal information has earned a classification as an asset of the business. Different types of information have immense financial value, and implications upon breach/loss, depending on the type of business, and the application of that information. Broadly speaking, Personally Identifiable Information (PII) includes; name, address, date of birth, social security number, email address, telephone number, username, password, car licence details, credit card details and photos., Personal Health Information, Intellectual Property, Transaction and Payment information/history, usage logs showing user behaviour, etc. The list could go on, but the point remains the same. With the ubiquity of the internet, personal data privacy and security are becoming bigger issues as cyber threats increase in volume and complexity. It is important for any position that has the responsibility of protecting this data to assess risk, invest in adequate remediation strategies in the case of a breach, comply with all available and applicable regulations around privacy, and create strategies to render the compromised information less useful if stolen.
Australian Privacy Principles (APPs), and the General Data Protection Regulation (GDPR) which is the standard in Europe at the moment, can be referred to as guiding principles.
Any citizen of the European Union, accessing Australian business resources, falls under the protections of the GDPR. This requires an awareness, and compliance with this standard if operating in that jurisdiction.
The next step would be to see how the worlds of Privacy and Security affect each other. A linear argument would say Security values Privacy, and seeks to protect it. Privacy is used to shield Identities, and these are Assets worth protecting. The implications of breaches of privacy in the Cyber Age are enormous, and unfortunately, organisations that traffic in private information (corporations specifically) are often not adequately valuing the Security around this. What was the last major cyber breach you heard of, where millions of user account information was compromised? As a person in charge of Security for an organisation which is a massive responsibility, it should be a question in the back of your mind at all times: are we the next target? The implications of a breach are often under-researched, and the risk of impact not adequately assessed. A lot of the time, there is a lack of ownership or accountability when it comes to keep a strong Security culture, one that is conscious of the many potential threats in its environment. The concept of a Privacy Champion is definitely one to consider. A single point of contact charged with the important task of encouraging and driving that Security awareness in an organisation or team.
The Impact of Privacy in Business Today
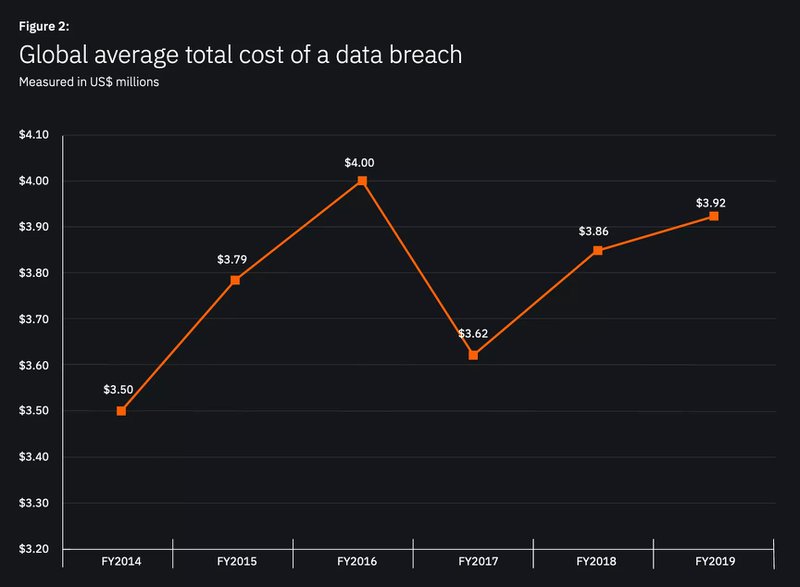
The world we live in has certainly become more connected through the advent of certain technologies, and at the same time less trusting of those connections. Security Consciousness is a mandatory part of any professional’s sphere, and many policies dictate how to treat other parties in relation to your business or entity. Firstly, it should be about valuing business assets correctly, including the cost of loss of information through cyber breach. Certainly, an impact assessment and historical information shows that some of the biggest organisations have suffered due to negative press and public perception. Public perception drives consumerism in business. If your business is associated with insecure practices, it will be felt on the bottom line. This issue has real money consequences, and often there is poor communication around this issue at the top of organisations. The answer ultimately depends on the country and industry but in general, can span anywhere from $1.25 million to $8.19 million. https://digitalguardian.com/blog/whats-cost-data-breach-2019
More than the negative financial impact, is the real world impact on the people who are often customers of these organisations. It can be argued that the issue of safeguarding privacy falls under Corporate Social Responsibility – due to the potential negative impact in many people’s lives.
The Beginning of Remediation
Generally speaking, it begins from the top. Guidelines and regulations published by governmental bodies charged with Security are a good start. Legal and jurisdictional regulations and requirements must always be consciously observed to ensure the business is operating safely in its environment. Adequate risk and impact assessments performed against existing infrastructure would also lend information to the decision making authorities. More of the right information is sure to increase positive impact in business operations. This is an issue worth investing resources into understanding and developing a mature operational framework around.
To understand this issue from the “bottom-up”, the first thing to do is to secure the “local” environment. This means ensuring that the infrastructure private data sits on, and the people in organisations that deal with sensitive information, are Security conscious. In terms of the network structure, as an example, we would be talking about border devices (Firewalls, Border Gateways, Filters, etc) and how they safely transact in information to the “outside world”. It is about ensuring that sensitive private data both at rest and in transit is adequately secured and protected by the technology it traverses. Best practice is assessing potential avenues of attack, namely, technological vulnerability and social engineering. Equipping the right people with infrastructure and training are important steps that observe the importance of maintaining the value of privacy.
By The Numbers; Statistics of Cybersecurity Cost
The cost per compromised record to a company, according to IBM, is USD$141, Accenture have it at USD$11M per year across 254 companies. The cost of breaches is no longer a question. Neither is the cost of protecting yourself from threats in the cyber landscape. It is said here, that if you are not actively protecting yourself, you are inviting attacks, as an easy target for malicious agents. The critical point, is adequately quantifying the risk parameters your organisation is prone to, and instilling appropriate controls and mitigation strategies proportionate to the risk identified. Even then, the most cautious would assume a “shadow” risk factor that is not easily identified or quantified. That will require further consideration by your Leadership team. The barriers of communication that commonly exist around this subject are one of the biggest challenges to progress, on a global scale. If we cannot get this right, we will continue to stay 10 steps behind the attackers.
The last thing to think about is building a federation of Trust between the Security champions of organisations. Whether it be the CTO, the CIO, the CISO, or any rank in between, creating dialogue around Security culture and awareness, and sharing information and strategies on common threats in the industry is an excellent way of furthering a safer business community. Forums of discussion disseminate information very efficiently, and if the leaders of Industry are using these platforms to further the cause of Privacy protection, everyone benefits positively. A Safer society is a better society for all.
An Ongoing Process
Privacy and Security often go hand-in-hand, and their evolution together and independently is never going to reach a final state – there’s always room for improvement.
Any company holding PII (and you likely are) should be taking both data privacy, and of course security, seriously.
If you wish to understand how you can improve your data privacy and security, reach out to Fort Safe today.