The Landscape
The internet is a very hostile place, with very few rules designed to keep the user base safe from malicious actors. All web-facing infrastructure faces a high degree of risk with regards to keeping out unauthorised access of data, especially Personally Identifiable Information (PII) and commercially sensitive information. With this in mind, it is crucial that any element of a web-facing system be designed with security at its core.
The Nuts & Bolts
The OSI model – Open Systems Interconnection – is a framework developed by the ISO that helps define how computing systems communicate, regardless of their underpinning structures or the type of technologies employed. There are 7 layers described. This is important to understand, even from a helicopter view, as the fundament network layer (3) security measures ensure that any device that facilitates packet flow has secure firmware, and handles packets in the expected manner. The Transport (4) Layer which facilitates TCP/IP communication (basically the part of the internet we get to see) basically has to do with packet structure and how applications handle information across interconnected and distributed networks. These elements have remained largely unchanged for a long, long time contextually speaking. They are reliable.
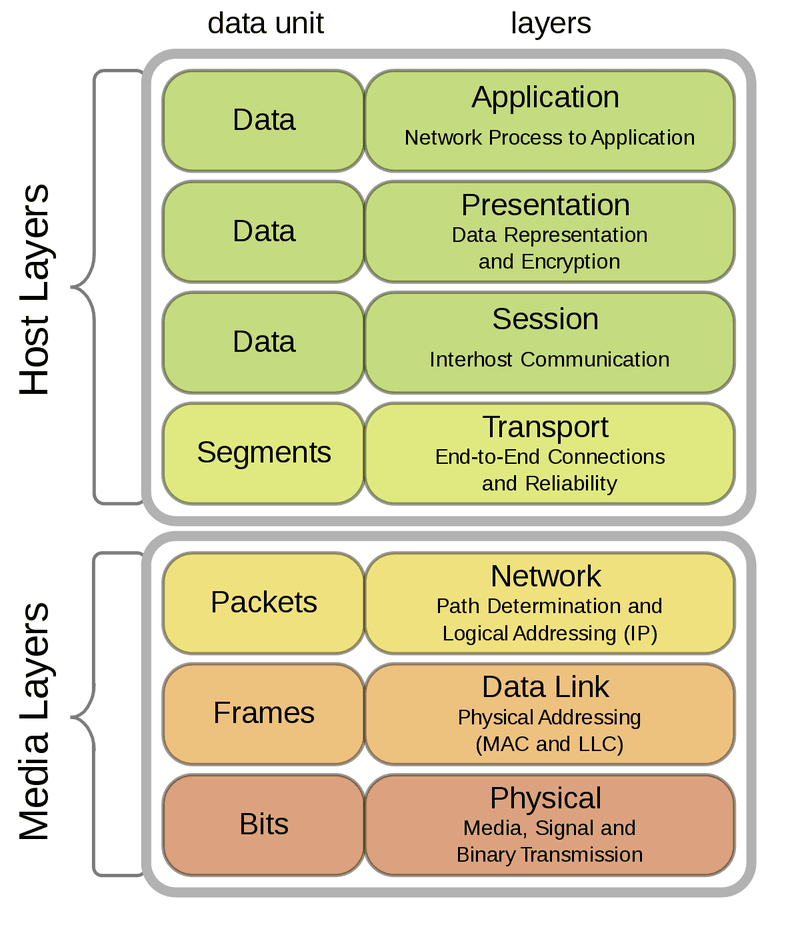
Now, as we hit the Session (5), Presentation (6) and Application (7) layers we start to introduce complexity. These three can be grouped together as the Data functions as their combined efforts facilitate web or user experience on the internet in the form of web applications or web-apps. It is here due to the inherent complexity and constant state of flux, that attackers find the largest surface area for attack.
Pragmatic Measures
Web applications are used for all sorts of operations – from eCommerce, to the hosting of audio/visual content, social networks, and information sharing, to name a few. The application itself is the client-facing object, and allows the user to access certain kinds of information. Depending on the nature of the application, and the information it serves, attackers will generally assess how the application is structured and built, what software (and hardware) it utilises, and inherently how secure it is against unauthorised access. The more sensitive the information, the more valuable, and therefore higher risk to any business or entity. Most complex applications have many different utilities as sub-components, and those sub-components can have several lower level dependencies as well. As attackers spend time attempting to penetrate a system, the likelihood of vulnerabilities being found at any level of the system increases exponentially. This leaves application owners with quite a challenge;
“How do we get and stay, secure?”
In the wild west of the Internet, a state of verifiable security is more a philosophy than a practicality. The constant emergence of new vulnerabilities ensure that one must continue to practice Security Consciousness, to minimise the possibility of malicious access. The first step, is to ensure that all internet-facing applications were designed, and coded with security as a core objective. There are different methodologies, and industry-recommended guidelines that can facilitate this process. It should be noted that this cannot apply to everyone. Not all entities require a coded application, and many of them being small to medium size cannot afford that exercise. A lot of utility is found in off-the-shelf applications repurposed for a particular brand or business. In this instance, even if the core application is designed securely, usability is grown by allowing open-source development of additional plugins and features. Many of these developers or creators are security-literate. If they are to create a plugin that facilitates business operation in any way, that risk profile must be taken into account and the (all too likely) gaurdian knot of code must be acknowledged.

So, What Can We Do?
Penetration testing is one of the best methods of independently assessing your infrastructure for security vulnerabilities. It is conducted by knowledgeable professionals whose prime function is to understand the landscape and popular/possible threats, get in the mind of the attacker and use key skills to simulate malicious access, and recommend remediation strategies that reduce overall organisational risk, and play a part in ensuring that core business function is not (drastically) affected by Security incidents.
With regards to Web Application Security specifically, the Open Web Application Security Project (OWASP) is one of the best knowns sources of information with regards to popular attack vectors, and known remediation techniques.
It is important to conduct an assessment and cross-reference the application’s function and features against known attack vectors or vulnerabilities. Once that is done, getting the appropriate remediation strategy is vital. In some cases, it is a “simple” case of patching a component to it’s latest version. This usually isn’t quite so simple because stability and dependency issues within the application itself; updating one part of it would destabilise core function. It can also be as complicated as looking at Source Code and implementing changes that change the nature of the application itself. The most important thing to the organisation is that independent expert-level assessments are conducted, the best possible remediation techniques are offered AND implemented, and a continuous security-conscious posture of review is upheld. Fort Safe are happy to work in partnership with organisations who desire to improve their security posture on all levels, and our Pentesting team are among the best in the industry. Speak to us about how we can help you and your customers operate more safely.
Zero-Day Vulnerabilities
A Zero-day (also known as 0-day) Vulnerability is a computer-software vulnerability that is unknown to, or unaddressed by, those who should be interested in mitigating the vulnerability (including the vendor of the target software). Until the vulnerability is mitigated, hackers can exploit it to adversely affect computer programs, data, additional computers or a network. An exploit directed at a zero-day is called a zero-day exploit, or zero-day attack.
One important core function of a good Penetration Testing team is to constantly stay abreast of Zero-day vulnerabilities. This is one of the benefits of this specialisation, and that has a flow-on effect on the clientele they are servicing. The most accurate, up-to-date information of vulnerabilities, combined with an intimate knowledge of your infrastructure, would serve an organisation very well in practicing business securely on the internet. The severity of some discovered vulnerabilities prompt live conversations around an organisation’s response strategy, and the implications (either direct, or indirect) to the business itself.
The best analogy here would be choosing a doctor who you see for a long period of time. They gain an understanding of your health over time, and combined with medical expertise, become adept at diagnosing new issues, or treating chronic ones. It is a question of the best information, delivered in a timely fashion, with the expertise that protects business interests. Continuous assessment, monitoring and management of live systems is what we recommend – in effect have your pentesting organisation on speed-dial. Making sure communication channels are open, clear, and collaborative goes a long way to making everyone safer.
Compliance
Certain business types are mandated by law to conduct security assessments of all publically-accessible/public-facing infrastructure. The critical factors are usually – the storage and usage of Personally Identifiable Information (PII), commercial customer data, health data, financial information, the conducting of business operations across jurisdictional boundaries, interaction with governmental entities, the list goes on. The kind of expertise required to ensure that the organisation meets its obligations and requirements is rarely found inside an organisation that does not have Security as a core business function. In order to exist in any environment, compliance measures are put in place by governing bodies with the safety of all who operate there, in mind. Many would understand that thriving in complex, competitive, and risky environments requires much greater attention and awareness.
Understanding requirements placed on the organisation, and employing the appropriate professionals like Fort Safe to assist the organisation’s compliance goals is our most recommended approach. We specialise in understanding not only the security landscape in general, but also in creating a tailored approach that keeps your organisation’s business mission and objectives in mind. By prioritising your needs, we are able to offer industry-leading advice that ensures your interests are protected. As the relationship grows, we can assist the future planning function of an organisation by lending expertise in the Design phase of projects. This approach minimises the need for drastic remediation measures in the future, and adds to the stability and integrity of business functionality.
Key Takeaways
Pentesting is an excellent investment for any organisation that operates on the internet. For all of the reasons above, it is critical that Organisational Leadership understand the implications of operating in this environment, adequately quantify the risk the business faces by not conducting regular Penetration tests, and remediates this gap accordingly.
You can never be too safe in this world, and as the “future” gets faster and faster technologically speaking, this is one of the best and only ways you can continue to operate safely going forward.