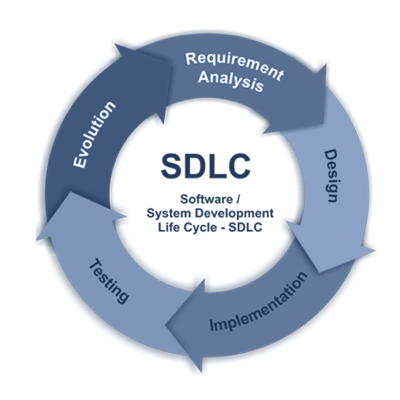
A SECURE DEVELOPMENT LIFE-CYCLE
No matter how many applications you have, we work with you to identify the risk of each application according to exposure, data sensitivity, function, technology stack, and more. Your organisation will be able to understand its risk profile and where to focus security efforts and budget.
We perform an SDLC gap analysis and identify the best security controls to be integrated into your SDLC. This ensures that your software development team consistently produces secure software.
Every member of our team possesses expert skills in application security offense and/or defense practices. We handle each client’s needs strategically.
Our customized approach to application security advisory, blue team, red team, or training engagements ensures that every interaction with our team is focused on improving the security posture of your organization and its software.
STEPS TO CONSIDER
Quality and security of customer’s applications, solutions, and products.
Proper and mature organisation of the software development process, including control and monitoring of the development process.
Mitigation of risks of unexpected expenses for software development and support due to clear requirements and design, resulting in the reduction of production scrap and rework.
Increased security awareness and the establishment of a mature security culture of software development.
Perform Threat Modelling Exercise using STRIDE and DREAD methodologies for secure SDLC
Perform Security By Design / Security Architecture Review
Perform regular Secure Code Reviews after each Sprint
Perform Fuzz Testing
Perform Penetration Testing
Perform Cloud Security Configuration Review
Create Incident Response Plan
Execute Incident Response Plan
SECURE YOUR SDLC
FORT SAFE’S PEDIGREE
If you’re ready to talk with us about your requirements, or need to unpack exactly what you should be doing, schedule a call with a Fort Safe Consultant today.
SDLC 101
Still need more details about Secure SDLC and what option may be best for your organisation?
Request a Free Consultation And Make Sure Your Business Is Protected
Book an obligation-free Vulnerability Assessment today.