RESPONSE AS A PROCESS
LEARN. ADAPT. OVERCOME.
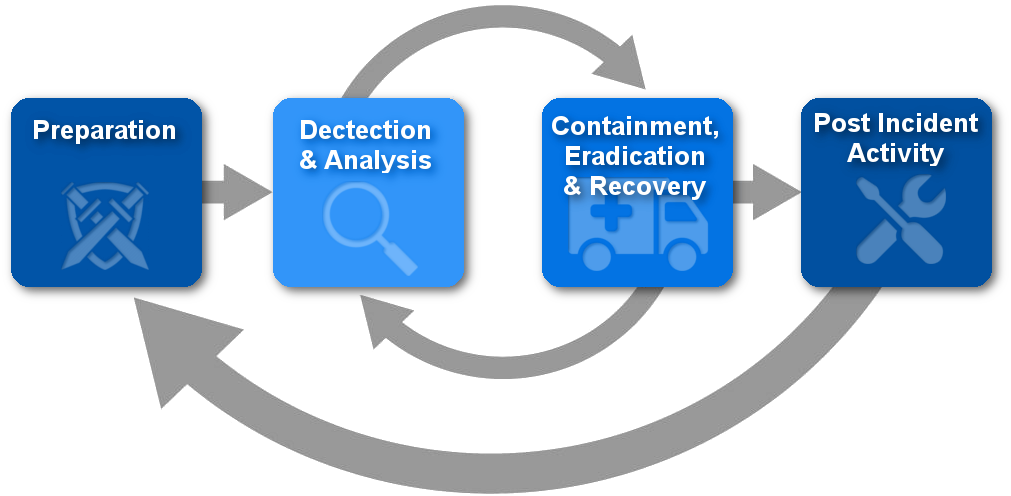
Security incidents and losses are on the rise, yet many organisations don’t have a plan in place to diagnose and handle a breach. While you can’t prevent every possible incident, our detection and response team can help you to respond quickly and minimise damage and downtime when attacks and exploits occur. We take a comprehensive and proactive approach to help you protect, detect, correct, and adapt.
The growth of technology has dramatically increased the risk of computer-related fraud and misconduct. When faced with investigative and dispute matters, it is important to understand the ways information can be stored, duplicated, corrupted and retrieved, and how best to manage it to ensure compliance with laws and regulation.
SPECIALIST AREAS
We can also assist you with advice in preparing appropriate details for an Australian Mandatory Data Breach Notification. According to IBM Ponemon Institute Third Annual Study on the Cyber Resilient Organization 2017, 77% of companies surveyed out of 2800 across the world do not have a Cybersecurity Incident Response Plan
Our digital forensics and incident response team use powerful information technology tools, insightful information management approaches and forensic data analytics frameworks to help you minimize risk, respond to investigative matters and optimize your business decisions. We provide on-demand, interactive analysis, reporting and exploration of data sets using advanced discovery processes and methodologies.
We identify, collect, recover, reconstruct and preserve electronic evidence to help both the business and legal community translate data into actionable knowledge that can be used as meaningful testimony in legal proceedings or in response to shareholder or regulatory scrutiny.
A DETAILED INVESTIGATION
Our incident response team goes beyond data collection and malware analysis to investigating your enterprise environment and discovering digital artifacts on all your digital and cloud drive devices.
Request a Free Consultation And Make Sure Your Business Is Protected
Book an obligation-free Vulnerability Assessment today.