The rise in visibility of enterprise cybersecurity risk has created a greater need for precision, accuracy, and timeliness in risk assessment models. As companies come to rely on Information Systems (IS) and Information Technology (IT), the risk inherent to its digital infrastructure rises. The risk matrix, a form of analysis that far predates computers, continues to become a more formal and important part of managing security risks.
The security risk matrix is a relatively recent yet increasingly important part of cybersecurity in businesses of all scales. Security guidelines published by the National Institute of Standards and Technology (NIST) include best practices that include these risk matrices as an essential aspect of risk calculation in given assessments. These assessments are used to prioritise, identify, and estimate the risks to individuals, external organisations, and organisational operations that occur with the common use of IS and IT.
What is a Risk Matrix?
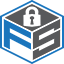
A risk matrix is an analytical tool used in many industries for risk evaluation. Using “probability” and “severity,” the risk matrix precisely quantifies the scope of hypothetical safety outlines and real-world scenarios. In general, quantification breaks down into three categories that are recognized by most businesses: Green (an acceptable risk), Red (an unacceptable risk) and Yellow (a risk that is defined through the acronym ALARP – As Low As Reasonably Possible).
Depending on the organisation, more colours or shades may be used for more distinct classifications. In order to maintain the standard, however, any additional colours usually help define only the visual aspect of the matrix rather than pointing to a fundamental difference in measurement technique.
Risk Matrix Standards
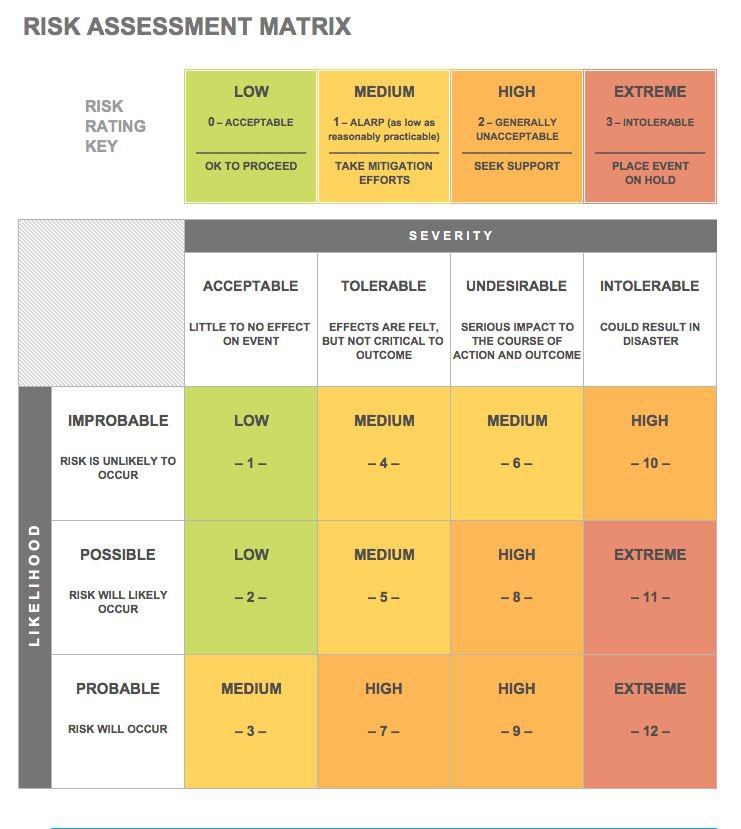
NIST Special Publication 800-171 defines cybersecurity risk controls that are used across industries. These best practices are used because the NIST found that portion of security controls to be the most relevant to the security of sensitive data in private enterprise. The building-out of a carefully thought-out Risk Matrix is an integral part of any Information Security Risk Assessment.
How the Risk Matrix Grid Breaks Down
The traditional security risk matrix is usually made up of a 5 x 5 grid which may increase or decrease depending on company scale and number of variables in the assessment. The final deliverable of the grid is the equivalent of a risk assignment number, which is a combination of the two axes Severity and Probability. This number represents the full scope of the risk.
The traditional risk matrix grid uses the X-axis as Severity and the Y-axis as Probability. In most cases, low Severity and low Probability began in the upper left corner of the grid. Risk matrices have the ability to move in any direction, which gives the tool flexibility in how it appears. Companies must define how different appearances of the matrix are interpreted. It is very important that these interpretations be consistent between departments and comfortable for all involved. While a risk matrix contains only two variables, but those two variables may be defined differently by different assessors.
Probability in a Risk Matrix
Probability is generally defined as the frequency or the likelihood of a particular situation occurring. In most risk matrices, the range of likelihood will move from “extremely rare” to “reported several times annually.” Each company may define its own range according to positions that are relevant to it.
Probability is useful in quantifying the following characteristics of a risk event:
- The likelihood that a certain event will occur;
- The likelihood of non-positive consequences from a certain event; and
- A total risk scenario probability, including how likely it is that the risk event and its non-positive consequences occur.
Risk matrices can be used with probability representing a likelihood of consequences or risk event probability. In the likelihood scenario, each scenario is usually assigned a letter value. A usually corresponds to low probability while the letter E represents high likelihood in the traditional ‘5 x 5 grid’.

Severity in a Risk Matrix
The definition of Severity in a risk matrix is usually more straightforward than Probability. Severity usually consists of the following components:
- How severe the impact will be in certain safety events; and
- Accounting for the more likely outcomes that will occur.
Severity is usually a range of numbers. In the traditional 5 x 5 grid, the numbers would start at 1, representing low severity, and moving up to 5, representing the highest severity. More precisely, the negligible 1 rating would represent low consequences and only a slight effect on business outcomes. 5 would be catastrophic, representing high financial consequences, mission aborted failure and possibly multiple fatalities.
Of course, any assessment that is overly high-end severity would warrant an extensive investigation.
Managing Security Risk with a Risk Matrix
The risk matrix has a specific purpose during a risk assessment. Companies may adopt slightly different approaches to the use of the matrix, but there are two primary ways in which companies will utilize the matrix. It is especially important to remember that the risk matrix does not make the decision for the company. Rather, the matrix is used only to prioritise activities to approach prevention of given outcomes. If we look at ISO 27001 A.16.1.4 or the corresponding NIST SP 800-53 Relevant Security Controls, the use of a matrix is fundamentally justifiable.
Moreover, a risk matrix should not be seen as a panacea – it is not a tool to use for making critical decisions. The simplicity of matrix highlights that it’s only designed to provide a point of comparison using the number letter combination from the Probability and Severity axes, nothing more. In a 5 x 5 grid, these numbers and letters may represent the following classifications:
- 1A – extremely low Probability and extremely low Severity
- 5A – extremely high Probability and extremely high Severity
- 4B – middle low Probability and middle high Severity
Using the number and letter system is an especially powerful historical assessment tool. Because risk has been quantified in a way that can be translated regardless of the scenario, previous incidents can be used to accurately assess future scenarios with much greater precision.
Why should a company invest in a risk matrix during a cyber assessment?
To be sure, there are numerous tools that can be employed to register quantifiable prioritisations during a risk assessment. The risk matrix is considered a best practice by assessment experts for the following reasons:
- Accurately identifying threat sources – The better you know where relevant threats are coming from, the more likely you are to prevent them. The risk matrix has the ability to accurately identify and prioritize these threat sources. The risk matrix also helps to explore the impact those threat sources create.
- Reduction in long term costs – Mitigating potential threats will help to prevent security incidents, which you can prioritize in order to point resources at the most important threat source. When these things are properly prioritized, companies begin to save money in downtime, repairs and maintenance on overloaded hardware and litigation from data breaches.
- Greater ability to self-assess – A proper digital risk analysis greatly improves security implementations and helps to reduce data breaches and attacks.
- Improving communication – Assessing digital risks properly means interdepartmental coordination. This helps to enhance communication between departments and increases overall organizational visibility.
- Compliance – More companies and never are investing in cyber insurance, especially in the world of small and medium-sized businesses. As it stands today, two thirds of all SMB’s without cyber insurance that suffer a breach will fail completely. Depending on your industry, you may also be required legally to maintain a certain standard in your cyber risk assessments. For example, the medical industry requires every entity covered under the Health Insurance Portability and Accountability Act (HIPAA) and (similar regional standards) to perform consistent assessments. Some industries also face compliance measures from industry bodies through to the federal government.
Removing Human Bias
Perhaps the most important reason that the risk matrix has been identified as a best practice is that it removes a great deal of human bias from the risk assessment process. Studies have shown that most managers are much more confident in their ability to assess uncertainty than they should be.
Decision-makers in these businesses may lead the organisation down the wrong path due to inconsistencies and discriminations they make from overconfident, nonqualified assessments. The risk matrix provides a framework that largely removes human biases from the equation when assessing important risks.
Egon Brunswick showcased just how effectively removing human biases consistently improved results. The ‘Lens Method‘ has been applied to many problems over the years, including changes in stock prices, cancer patient recovery and business failures. All of these resulted in a huge reduction in errors and consistently brought more beneficial results than experts could create on their own through unqualified assessments. With skilled assessment, a security risk matrix can be an equally effective measure for your organisation to offset any cognitive bias and ensure a basis for sound decision-making.
The simplicity and accessibility of a security risk matrix will continue to prove invaluable to organisations for years to come. The important step is to ensure the precision and accuracy of its creation adoption to steer risk assessments in the future in order to reduce human error and improve business outcomes.
If you wish to understand how a security risk matrix may help your organisation, reach out to Fort Safe today.