Data and security breaches can result in the loss of significant financial resources for individuals and organisations. According to IBM, The average cost of a data breach is USD$3.86 million. When hackers steal data, it usually includes sensitive personal information that they can use to commit financial fraud, identity theft, or other serious crimes. Data breaches can sometimes take months (or longer) to detect – surprisingly, it’s estimated the average time for an attacker to have unfettered access to systems – the mean time to identify (MTTI) – was 197 days before they’re discovered. By the time many attacks are detected, victims’ sensitive Personally Identifiable Information (PII) can already be in the hands of dozens of unauthorized individuals through dissemination across the dark web, or has already been used to commit fraud. It’s vital to have a well articulated incident response plan.
With the proliferation of data breaches, organisations can take several steps to help mitigate damage when they do inevitably happen. Further, IT teams in organisations can also leverage some of the steps to help guard against future attacks. By identifying and correcting vulnerabilities related to human factors and processes, organisations can learn from the incident and make improvements.
Initial Identification of a Data Breach
The first step in managing a security breach is to determine the scope of the breach. Identifying a security incident involves finding out which systems, services, applications, or devices have been impacted. Identification also involves determining whether the incident was initiated by human, process, or equipment error. For instance, is the breach isolated to the company’s email system or has it impacted other internal resources such as shared network drives and servers? Did an employee download a questionable email attachment or click on a suspicious link that subsequently spread to more than one employee? Did the attack come from someone outside the organisation? There are even mandatory compliance requirements like CPS 234 that dictate what details and when governing bodies must be notified.
While attribution is incredibly difficult, it can help to determine the target and type of attack. Sometimes a data breach can originate from an employee or vendor unknowingly compromising systems with malware from a phishing campaign. Similarly, the exact same occurrence may have been intentional, and therefor much more likely to happen again. The ramifications of leaving the root cause unaddressed can be dire, and thus remediation in terms of immediate triage and long-term resolution are going to be significantly different.
First Things First in Incident Response
It is critical for IT teams to quarantine or isolate the attack’s damage as quickly as possible. Contacting law enforcement and government agencies such as the Office of the Australian Information Commissioner should also be included in the organisation’s immediate response. Having a well documented Incident Response Plan – or an Incident Response Playbook – is of paramount importance. Delays in communication can rapidly erode trust and allow investors, partners, and industry commentary and the media to start pecking away and undermining confidence at a precipitous rate. It’s imperative for any organisation to speak with experts like Fort Safe to start taking steps to either create or evaluate and evolve their Incident Response Plan.
The organisation’s legal team should double-check relevant privacy laws and regulations related to the reporting of data breaches. These laws can vary according to the nature and extent of the breach, as well as the organisation’s main location. Applicable privacy laws can determine how firms respond to and handle a data breach’s aftermath. The organisation will need to follow and implement an incident response plan when responding to a security incident. The plan needs to include the guidelines and stipulations determined by government agencies and laws. These guidelines often include public notifications and announcements of the nature and scope of the security incident. For example, potentially impacted individuals may need to be notified by mail. Press releases distributed through news networks can also help inform the public, but organisations should not rely on releases as the only means of notification. Include details of who may be impacted, the nature of the information that may be compromised, and steps potential victims can take to rectify any damages.
The Recommended Response Sequence
- Identify and stop the breach by isolating any impacted systems or user accounts. This often entails disconnecting these systems from the network or temporarily suspending user accounts until passwords can be changed. In more severe cases, entire departments may need to be taken offline until the damage can be corrected.
- Determine the nature and scope of the damage by conducting an investigation. Looking for malware and remove any traces by conducting more than one scan. Keep in mind, preserving memory, storage and system logs is important for forensics. Fort Safe can help with your security incident response and determine what data was compromised and its sensitivity level.
- Employ forensic experts to isolate and document the damage by backing up evidence of the attack. If the attackers used malware, compare backups prior to the attack and after the attack. Ensure that any backups containing evidence of malware are isolated from the network and other systems.
- Determine who the organisation needs to notify and how. Leverage an internal or external public relations team to help prepare and execute a communications plan. Be sure to follow any legal reporting requirements, but also determine exactly what type of information is appropriate to publicize.
- Perform a security audit and re-secure network resources prior to placing them back online. It’s critical that an organisation uses their internal teams and uses an external audit function to check systems multiple times before determining the systems or user accounts are safe to restore. If applicable, user education about social engineering tactics and password precautions should be implemented prior to restoring accounts. At a minimum, passwords should be changed and new, more secure password rules implemented. The IT team will also need to ensure the latest security patches are installed on all systems and any configuration errors are corrected. It’s important to then enhance protections with measures like Two-Factor Authentication (2FA) to halt any repeats of incursion.
- Based on the results of the security audit, update processes, incident response plans, and employee training. Hold meetings to review security controls on where and how to improve, as well as evaluating privacy policies to improve overall security posture. Notifying any third-parties of protocol changes should also be addressed concurrently. Implementing employee and vendor training to review appropriate prevention methods and the importance of maintaining security measures.
You can talk to Fort Safe to create a custom Incident Response Playbook for your organisation
A Clear Communications Plan
An organisation will need to implement a detailed public relations and communication plan, depending upon the scope of the attack. A public relations and communications plan can include press releases, interviews with newspapers and television stations, announcements on the firm’s website, press conferences, and individual letters or emails targeted to those whose personal data may have been compromised. Those who have been impacted, including third-party organisations, employees, and clients should be notified before the general public. The police and the Office of the Australian Commissioner should also be notified as soon as possible. If an organisation does not have an internal marketing or public relations department, it is best to consult with a recommended public relations agency prior to making any public announcements. While the agency will often handle the formulation and execution of the plan, participation and input from company representatives will be necessary. We can see when executed correctly like in the case of the recent Norsk Hydro attacks, the impact can be lessened through transparent and apparent communications.
So while most enterprise organisations have a PR/communications team (or consultancy) that handles any external stakeholders, it’s very common for any communications piece to be 100% reactive in the face of a breach. By addressing this gap ahead of time, the organisation can have a response and communications framework ready that can facilitate the release sooner. These hours (or perhaps days) of difference can be invaluable, and fly by awfully fast if the organisation is put in the position where it’s purely reactive.
Learning and Adapting
After the firm has communicated the nature of the breach and notified all impacted parties, it is critical to learn as much as possible from the attack. Cybersecurity incidents usually occur due to inadequate processes, human error, weak and insecure password practices, system vulnerabilities, and successful phishing or social engineering attempts that install malware. The IT team should identify weaknesses and vulnerabilities in the firm’s incident response plan. If the firm does not have a plan, one should be designed, documented, and reviewed by a company like Fort Safe. The plan’s design should assume that a future attack will take place, especially since hackers tend to attempt subsequent attacks on organisations that have already been compromised. Preparations should be made to re-train employees, implement more robust and secure security procedures, limit or restrict internal and vendor access to network resources, closely monitor data, and implement security methods including two-factor authentication and encryption. Be sure to document how to prioritise various types of incidents and include written guidelines. Incidents can be prioritised according to functional impact, information impact, and ability to recover. Part of the learning and adaptation process can include consulting with external experts that specialise in cybersecurity attack prevention.
Regularity
While all the preceding and following ideas will absolutely help in the shaping and evolution of your security posture, what can really expedite your maturity and capability in incident response is frequency.
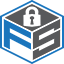
If we run with the ‘evolution’ metaphor, the shorter the lifecycle of the animal, naturally, the more opportunity for evolution during an absolute period of time. By examining our cyclical processes as defined in image 1.1 ‘The Incident Response Cycle’ and where we can expedite our Learning and Adapting processes to influence and further our Incident Response effectiveness.
While there’s no right answer for every organisation, a commitment to regularity – and a periodic review of the outcomes (p 25.) and pace of these cycles – is essential. By spending time internally, and ideally with an external consulting capability, you can review the execution of each cycle and adjust cadence as needs dictate.
Final Thoughts
Data breaches can result in detrimental damages to any organisation, but smaller firms are especially vulnerable. Norsk Hydro lost an estimated USD$50 million due to losses in productivity, not due to the impact of any erosion of trust on their share price, and the the global average cost of a data breach is still hovering around $3.86 million. With 215 notifications reported in Australia last quarter, with 85 of them in just the Health and Finance sectors.
The full impacts from a data breach still aren’t being realised, with most just ascribing the obvious surface damage as the only real issue. The erosion of trust from customers – and in some cases partner organisations – can be an even more profound affect. This breach of Landmark White did not involve PII, and wasn’t even a typical hack, but rather “the deliberate acts of a person known to LMW” further highlighting the gamut of implications a business must consider in the face of a breach.
Developing and executing a thorough response plan according to government guidelines can help mitigate an attack’s harmful effects. While identifying and stopping the attack from spreading throughout the organisation are vital, the ability to learn from the incident and make necessary improvements are even more important when it comes to preventing future occurrences.
Talk to Fort Safe today to start building and evolving the way your organisations responds to incidents. Before you wish you had.