Ransomware is more dangerous than ever. It hits businesses of all sizes, hospitals, government agencies, and not without irony, even crime investigation labs. It has become an organised criminal enterprise, with malware packages available through online darkweb marketplaces to threat actors with little technical skill. Its cost is huge and mounting, and victims face the choice of giving in to its demands, finding a way to recover their files, or cutting their losses.
What is the state of ransomware today? Who is most at risk? What measures guard most effectively against it? This article will bring you up to date on the changing threat landscape and help you to understand how to minimise its risks.
An Overview of Ransomware
Ransomware is defined as malware which encrypts some or all of the contents of a file system and subsequently demands a payment to provide means for decryption. Most often it relies on asymmetric public-private key encryption. It encrypts the target files with the public key of a public-private pair, and the private key is required to decrypt them. The demanded payment for decryption is overwhelmingly in Bitcoin or another cryptocurrency so that payments are transferred into an anonymous wallet; difficult to trace and even moreso, to acquire reliable attribution.
A Brief History

Joseph Popp devised the first known instance in 1989. He distributed his malware on 20,000 diskettes to attendees of a World Health Organisation conference on AIDS. It encrypted files on the victims’ computers and demanded a payment of USD$189 to a post office box in Panama. It used weak (symmetric) cryptography that could be reversed without giving Popp money. None-the-less, it was a successful proof of concept, and set the baseline for a new dark industry.
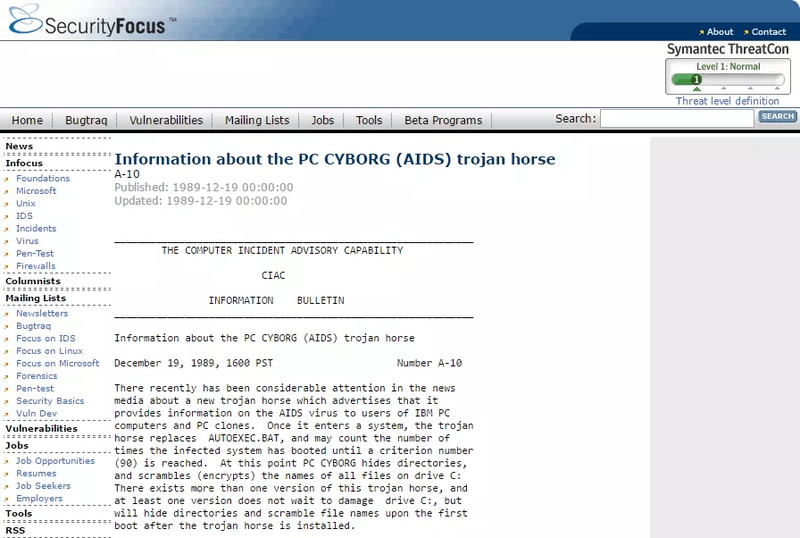
Ransomware began to be noticeable on the Internet around 2006 and became a major problem in the past decade. The appearance and popularity of Bitcoin made the (mostly) anonymous collection of payments possible. In late 2013, Cryptolocker elevated ransomware to a new level in terms of damage and costs to organisations (and individuals) by compromising over 250,000 systems. It required a dedicated and cooperative international team to take down the botnet responsible for its distribution in the early part of the following year. Unfortunately, like the hydra, several more sophisticated threats rose to take its place.
The most detestable of attack targets are inarguably hospitals. The most vulnerable members of society are deliberately leveraged by attackers, as withholding the provision of critical services is essentially; ‘pay us to remove the existential threat to those in your care, and by extension to your reputational and operational security’. Despite the abhorrent nature of such targets, there has been a spate of such attacks month in and month out with the healthcare industry making up
More recently, we’ve seen manufacturing infrastructure attacked, with Norsk Hydro at the focal point of a ransomware infection estimated to have cost the company over USD$40 million. And of course, the seriousness of malware infecting critical infrastructure like in the case of the Triton attacks foreshadows potential similar attacks with inherently catastrophic impacts held in check only by Bitcoin payments.
How Ransomware Is Delivered
Any of the methods of depositing malware on a computer can be vectors for ransomware. Phishing messages are the most common. Opening a link or attachment runs a simple loader which contacts a server. Usually the loader makes some checks on whether it should run. Perpetrators often don’t want it to run in their home country, so they can place geographic restrictions. Aside from not wanting to be caught too easily, ransomware operators are sometimes in league with their governments.
It has become increasingly common for campaigns to target specific victims and use “spearphishing” emails to make their messages look legitimate and safe. Rather than running scattershot operations, ransomware perpetrators are increasingly looking for a big return from a well-researched target, such as a government agency or a large corporation.
Ransomware can affect devices which people don’t typically think of as ‘computers’. Canon DSLR cameras have been shown to be vulnerable to ransomware and other malware. Such devices often don’t get a careful security assessment before being released. Untrusted and unauthorised devices connected by Wi-Fi can use the Picture Transfer Protocol and engage in various types of harm, including the encryption of pictures. No exploit of this vulnerability has appeared in the wild, but Canon has recommended not connecting its cameras to public networks. The protocol is a widely used ISO standard, so other manufacturers’ cameras may be vulnerable.
So there are myriad ways and endless variations by which devices may become compromised, limited by large only in the imaginations of attackers.
The Latest And Biggest Threats
A few years ago, many independent criminal groups created their own ransomware and spammed as many potential targets in hope of success. Now, a handful of variants have risen to prominence, and they’re available to small-time criminals as Ransomware-as-a-Service. GandCrab and Cerber are widely known examples of RaaS. The group behind GandCrab claims to have retired, but it is suspected they may just have moved on to a new code base. Many believe that state actors have used ransomware as a demonstration of power.
SamSam was one of the biggest threats. The organisation behind it conducts targeted attacks and demands larger sums, often in the tens of thousands of dollars, than most. It targets Java-based servers with outdated, vulnerable software. Once it has infiltrated a server, it compiles a list of hosts using the server and distributes the malware to them. SamSam was the seemingly the work of two Iranian men and has largely disappeared from the wild since the criminal charges were levied against them. Other variants like MSIL and Samas have been on a slow-boil for some time, but have yet to take over. A (much) newer threat based on SamSam, Spora, may prove to be the most damaging of all, but its too early on to predict with any fidelity.
WannaCry was notorious for a couple of years, but it theoretically stopped being a threat when a “kill switch” server disabling it was discovered. However, it is still active, causing large amounts of damage – in fact it is still the number one most common family of ransomware with over 25% of the attacked users. Systems with up-to-date software are mostly safe, but many organisations are far behind in patching their software. Some devices, especially IoT components, are difficult or impossible to patch, meaning some industries – like healthcare – are inherently more prone to compromise.
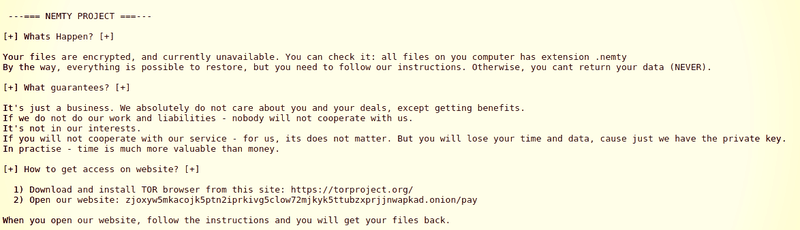
Most recently, we’ve seen the rise of the ‘Nemty’ family of ransomware seems to be delivered through unsecured instances of the Remote Desktop Protocol (RDP). This removes the victim from the initiation process typically started through clicking on bait from a phishing campaign or similar, and allows the attacker to just find the right entry point through RDP.
The price of Bitcoin has risen (and fallen, and risen) spectacularly in the past year. Attacks that demand a specific Bitcoin amount have become correspondingly more expensive as many forms of ransomware set their demand values back when the price was in the hundreds of dollars, rather than the thousands as it is today. The increasing use of targeted attacks is another factor pushing the average demand higher, as they typically have more leverage due to the greater intelligence they have from investing in footprinting their targets. These more targeted attacks are also contributing an increased threat-level for those organisations that may be targeted, as these focused efforts require equally focused defences.
Efforts To Stop Ransomware
The magnitude of the ransomware threat has spurred industry groups to take coordinated action. The United States’ Cybersecurity and Infrastructure Security Agency, National Governors Association, and other groups have issued a joint statement stressing the importance of defences against ransomware. The document recommends three steps:
Similarly, our domestic body, the Australian Cyber Security Centre (ACSC) – part of the Australian Signals Directorate (ASD) – has issued advisory documents to curtail the incidence and spread of ransomware attack. Both of these efforts can be distilled into the following critical steps;
- Offline backups of all critical sites and assets
- Employee training to increase awareness of phishing and other malware vectors
- Including external ‘first responders’ in cyberattack response plans

Paying ransoms encourages more ransomware. Government and industry organisations have been urging their members not to pay the criminals. Malware research organisations work to discover the latest threats and find ways to decrypt files without the attacker’s cooperation. Many types of ransomware are crackable and reversible. Ones based on custom code are more likely to be breakable, just as any form of homebrew encryption is. A victim should always check the current availability of decryption remedies before taking more drastic action. Attacks using strong, well-implemented asymmetric encryption are very hard to crack, though.
How To Protect Your Systems
Ransomware is often just one part of a malware attack. It can distract attention and resources while a backdoor continues to run even after the affected files have been restored. So total focus on a wholistic scope of defence is still required.
The most important protection is frequent offline backups of all important files, and these backups should not be directly accessible through file system access. At the enterprise level, this is typically part of BAU, but due to the complexity of such environments, it’s possible vectors may still exist.
Also very important is keeping all software up to date with security patches. Ransomware very often exploits vulnerabilities in old code releases. Once vulnerabilities are announced, criminals know about them and will find ways to use them.
Anti-malware software will identify and stop known forms of ransomware. New ones, including minor variants to evade detection, keep showing up, so it has to be regularly updated. Some packages use behaviour-based detection, so the act of altering files will trigger an alert. Some keep private, protected backups of files to aid in recovery.
Security awareness by everyone using the systems is an essential part of protection. Users should understand how phishing email works and avoid clicking on suspicious attachments and links. Spam filtering will keep many of those messages from reaching people’s inboxes. They can’t open what never reaches their mailboxes. Employees should know that it’s almost never a good idea to enable application macros to read files they’ve received over the Internet.
System administrators should issue access permissions on an as-needed basis. If an account doesn’t have write access to a directory, malware that infiltrates it can’t encrypt or delete those files.
There is no magic bullet against malware. Protection against ransomware and malware in general requires defence in depth. A comprehensive security system will aid in prevention and remediation and prevent potentially disastrous losses. If you wish to define a comprehensive path to prepare against ransomware and other security and operational threats, speak with Fort Safe about developing your own roadmap for better security.