Developing a Security policy doesn’t require reinvention. Several sets of guidelines are available, such as the CIS security controls, and the OWASP security design principles. The Australian Cyber Security Centre offers the Essential Eight, a set of flexible mitigation strategies to make systems more resistant to being compromised and that can be implemented according to an organisation’s appetite for Risk. These principles focus primarily on software management, and fundamental measures for securing your organisation.
Data breaches can be disastrous, resulting in both high direct and indirect costs, and a large negative impact to productivity. A huge portion of breaches are attributable to neglecting the application of otherwise preventive measures, such as patching. Following the recommendations of the Essential Eight may well prevent a major incident for your organisation.

In Cyber Security, the term ‘mitigation’ typically refers to methods of reducing or ending the damage caused by a security incident through proactive measures, or as part of Incident Response. The strategies described here are mostly about prevention, not damage reduction. They are mitigation strategies in the sense that they will reduce or eliminate the impact which a Security event might cause. If a phishing message tricks an employee into opening a malicious link, or if someone receives and opens a malicious document, following the Essential Eight makes it less likely any issues will follow, or there is at least a reduced level of potential negative impact.
How to Apply the Essential Eight
Every environment is different. The same set of priorities and actions won’t apply in every situation, nor for any company. The Essential Eight is a framework for a Security strategy, not a mere checklist of ‘things to do’. A Security plan needs to take into account the degree of acceptable risk and the nature of the risk. Some of the strategies are basic needs which are perilous to ignore, but some may not be applicable to every (Technology) environment.
Applying Security strategies is an ongoing process. A network is a living entity, and continues to change and evolve as devices are added and removed. New threats appear in software, and new defensive measures become necessary. The process is a matter of pursuing an optimal state of vigilance or awareness/readiness that doesn’t stand still. It is not a matter of reaching a static state or measure, and claiming victory.
The ACSC defines three maturity levels for the application of the strategies. Which one an organisation should aim for depends on its level of acceptable risk and the available resources. ACSC recommends as a baseline that all organisations aim for Level 3, while some need even higher levels of mitigation.
Preventing Malware from Running
Four of the strategies are aimed at preventing malicious software from being installed and running on an organisation’s systems.
Application Whitelisting
The first one listed, Application Whitelisting, is the most controversial. Whitelisting allows only approved applications — that is, ones which match particular signatures or are digitally signed by an authority — to be installed and run. There’s no question that it is effective in keeping malicious code out. It also requires resources to manage and can inconvenience users.
Operating Systems such as Mac OS and Windows allow setting up a simple form of whitelisting. When enabled, it accepts software that comes with the operating system or from the application store and rejects other software by default. Administrators can approve other installations. Third-party Security software is available, which allows Administrators to create custom lists of approved Applications.
Companies should test a whitelisting system before deploying it to make sure it works without interfering with normal core business operations.
Application Patching
Patching Applications is straightforward. There are no excuses for ignoring it. All software has flaws, and some of them endanger the security state of the organisation. When the risks become publicly known, someone is sure to take advantage or vulnerability and exploit them.
ACSC recommends using the latest versions of applications and applying “extreme risk” patches within 48 hours of their availability. Patching is necessary not only for applications but for runtime systems. If the currently installed Java or PHP runtime has a critical defect for example, it needs to be updated as quickly as possible.
Any patch needs testing to make sure it was applied correctly and there are no compatibility problems with the Standard Operating Environment at that time. If a compatibility issue prevents an application from being updated, it needs to be addressed at the earliest possible opportunity.
Application Hardening
Some applications have features that are more risky than they are useful. If they aren’t needed, disabling or limiting them can greatly reduce vulnerability to common attacks.
Browsers and email clients directly access the Internet, so they deserve special attention. Flash is obsolete, and it should be removed or disabled. Regular users shouldn’t be able to install unauthorised plug-ins. Other plug-ins improve security and should be installed by default. For example, ad blockers don’t just decrease annoyance; they can block malicious third-party content, known as “malvertising.”
OLE in Microsoft applications often isn’t necessary. PDF viewers generally don’t need to enable JavaScript. Disabling features like these reduces the opportunities for a rogue document to trigger malicious actions.
Restricting MS Office Macros
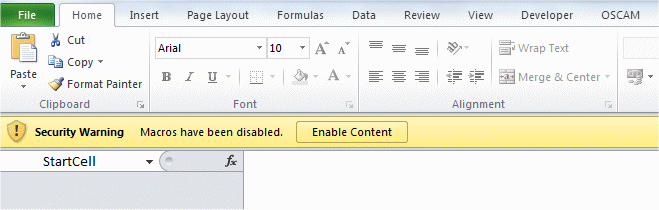
The Essential Eight list breaks out one form of application hardening for special attention. Macros in Microsoft Office documents let the application run embedded code, which is potentially very dangerous if the documents come from an untrusted source. Macros can run arbitrary commands if enabled.
Recent versions of Office disable macros by default, unless they have a signature from a trusted source or were created on the same computer. The important thing is to make sure these settings aren’t changed. The same issue applies to alternative/analogous applications, such as LibreOffice, which can open Office files.
Limiting the Impact of Security Incidents
Three of the Essential Eight strategies are closer to mitigation in the usual sense. They provide ways to reduce the chances of damage if an account is compromised or malware gets to run.
Restricting Administrative Privileges
Accounts that allow sensitive operations should be as restricted as possible. Only people who are trusted and need to perform those actions should have access to the accounts. Anyone who breaks into them, or gains unauthorised access by other means can do serious damage.
Role-based authorisation limits what a middle-level administrative account can do. For example, an account that needs to modify a database directly may not need the ability to create and alter user accounts. Tailoring roles to employees’ job descriptions will slow down anyone who breaks into their accounts, and limit the potential impact of this type of breach.
Administrators should use privileged accounts only when necessary. They shouldn’t use them for routine tasks such as email and Web access. The less they use the privileged account, the smaller the chance it will be compromised.
Multi-factor Authentication
Passwords can be guessed or stolen. Adding a second authentication factor means that password theft alone isn’t enough to access an account. Multi-factor authentication is valuable for privileged accounts and for remote access.
The most common forms of Multi-Factor Authentication (MFA) are typically Two-Factor, or 2FA and include the likes of sending a code by SMS or email – a seperate communications channel that helps authenticate Identity. Other methods, such as a dedicated application or a hardware dongle, are more secure, though they may be less convenient. Security questions such as “What is your mother’s maiden name?” are not sufficient, since the answers are often easy to guess or discover. Marrying together one or more additional security measures of this type provides an exponentially greater level of protection, without necessarily having to leverage advanced and complex technologies such as Biometric verification.

Operating System Patching
Applying Security patches to the Operating System goes along with patching applications. If anything, keeping the OS patched is more important, since exploiting a system-level vulnerability could give an intruder access to everything on the machine, and connected/associated machines.
Most major operating systems allow automatic updating. Administrators need to verify occasionally that updates are actually happening. A configuration error could stop them without being noticed, and indeed this issue has been known to be the catalyst for breaches historically.
ACSC’s advice is to use the latest version of the operating system, but this isn’t always necessary, nor even practical. What is important is to use a version which is still supported by the vendor. If it is approaching end of support, it should be replaced well before the last moment, so that any problems caused by an upgrade can be remedied.
Recovering Data and Systems
The last strategy in the Essential Eight concerns being able to recover from an infection or other damage to the system and data. ACSC’s Maturity Model recommends daily backups which are stored offline and retained for at least three months. Backing up once a day is a bare minimum. Incremental backups every hour – or even more often – will reduce the amount of data lost in the event of a disaster, though this will be dependant on the scope and variability of your particular operations.
The ability to restore backups needs periodic testing. The worst time to find out that a backup wasn’t operating properly is when it is needed. Downtime while figuring out how to restore damaged files is inherently very costly to any organisation.
Final Thoughts
Maintaining Cyber Security requires effort and imposes some inconvenience on users, but the cost of a data breach is typically measurably worse. Each organisation needs to do its own Risk Analysis and determine what actions will make its systems sufficiently secure. The Essential Eight strategies are a tested and useful framework for formulating a Security approach for your business. Be aware though, that much like any valuable framework, or indeed any piece of advice, the fundamentals – in the case of ITSM and General Operations Management – are to know the basics and execute them well.
To understand how you can roll the Essential Eight into your security strategy, talk with Fort Safe today and secure your tomorrow.