The cybersecurity of critical infrastructure, like power grids, the water supply, and air traffic control, is an ongoing, and very real concern for every nation. A successful attack on its data systems could have crippling effects and even cost lives. For this reason, the United States President Barack Obama issued Executive Order 13636 in 2013, calling for the development of a framework guiding the cybersecurity practices of private organisations involved in critical infrastructure, and this was the genesis of the NIST Framework.
The National Institute of Standards and Technology (NIST) responded to this with the Framework for Improving Critical Infrastructure Cybersecurity, released in February 2014. By NIST’s own statement, it isn’t just the providers of essential services that can benefit from it. It’s an excellent set of guidelines for any organisation that needs to protect itself from cyberattacks. It isn’t a set of legal requirements, nor is it a list of technological actions. Rather, following NIST for application security entails an organisational approach for determining and evaluating an overall course of action.
The Purpose of The Framework
Every organisation with sensitive data on its network is at risk. This covers anything from IP and telephony networks, through to databases with customer information containing Personally Identifiable Information (PII). While any area within corporate environment can inevitably benefit from a systematic process to maximise their security efficacy, there needs to be a way to prioritise the risks they face.
The framework’s aim is to define a set of processes to achieve better security. While there’s no such thing as perfect security, a business has finite resources and can apply them to where they will do the most good to improve their overall security posture. The NIST framework outlines how to evaluate the security position and choose the policies and processes that provide the best return for the effort. Afterall, being successful in areas of less importance isn’t a good use of resources if it means neglecting more important ones. The NIST framework is a ‘living document‘ and will continue to be revised periodically based on constructuve industry feedback.
A 6-Step Process
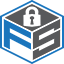
The framework doesn’t describe a series of steps to take and be done with, rather, it presents an iterative process. Each part is fuelled by a feedback loop from the others. These six steps will let an organisation develop its own cybersecurity profile based on the framework, implement it, and keep improving it as part of an ongoing cyclical process;
- Identify software and hardware assets. You need to know what applications and systems you have and keep the inventory up to date. “Shadow IT” weakens security if people are using systems and applications that the IT department doesn’t know about.
- Identify risks. Given the nature of the business and the state of the assets, the next step is to figure out where the most important risks are. What is exposed on the Internet? What would hostile parties like to get at? What flaws exist in existing practices?
- Prioritise risks. Resources, including time and money, ought to be allocated where they’re needed most. This requires identifying which risks are most important. The importance of the asset and the degree of vulnerability figure into the calculation.
- Create current and target profiles. The risk information should come together in a profile describing the assets, the risks, and the measures in place to deal with them. The current profile describes the existing state of affairs; the target profile defines a goal to aim for.
- Develop a detailed plan. The profile acts as a road map for designing specific steps for prevention, detection, response, and recovery. These procedures let managers and administrators know just what they have to do, both on an ongoing basis and when a problem arises.
- Keep up with change. The actions taken will change the risk situation. Once effective measures are in place against a certain threat, such as ransomware, it should drop to a lower risk level. Managers and technical people can then focus their efforts on the risks which are now at the top of the list. Changes in business operations and the emergence of new threats also change the order of risk priorities. This aspect of the framework should be thought of as a living entity. Every second in operation presents a new set of challenges and risks. The most optimal way to adjust to this landscape, is to invest time in a system that adjusts itself as much as possible, in relation to its environment. Effective systems of Communication, attention to Assets and their vulnerabilities (especially publically known ones), effective remediation techniques, and accurate and realistic accounting of (potential) impact.
The Framework Core
Three main areas comprise the NIST Framework: the Framework Core, the Implementation Tiers, and the Framework Profile. The Core is a high-level description of standards and practices for an organisation. It consists of five functions, which are further detailed by categories and subcategories. These functions aren’t sequential steps, though they may look that way. They emphasise preparation, not reaction. They’re all part of being ready for whatever may happen, and the actions they subsume need to happen before a crisis. A posture of Cyber-Resilience is the most prepared, risk-aware way to operate. It allows you to prepare for potential impact, and have at the ready, remediation strategies that both minimise overall risk profile, and the potential damage to Operations.

Identify
The question here is “What do we have?” The starting point is identifying applications, systems, risks, and requirements. This step includes asset management, risk assessment, and risk management strategy. This is where management determines what needs protection most urgently.
Protect
For this function, the question is “How do we keep it safe?” The inventory and the risk assessment lead to the implementation of safeguards against risks. This is a very broad area, including both technological defences and habitual human behaviours. It covers protective software, firewalls, gateways, Web Application Firewalls (WAF), access control, training, secure storage and transfer, code reviews of applications developed and deployed, and many more.
Detect
Dealing with this function means asking, “How do we find out when something goes wrong?” The detection methods need to be in place before it does. This area covers monitoring, file scanning, identification of anomalous events, and analytics. This function typically includes elements like Intrusion Detection Systems (IDS), a Security Operations Center (SOC), log management, etc.
Respond
Here the question is, “What will we do when something goes wrong?” The required actions are dictated as much by laws, regulations, and policies as by technological considerations. Clear plans need to be in place so that the response is efficient and free of panic. Systems may have to be shut down. Users and authorities may need to be notified within a short time frame. This function covers planning, mitigation, and improvements to prevent a recurrence. Having a sound incident response plan is critical – every company can and will be compromised. By way of example, if (when) an employee succumbs to a phishing scam and their machine is compromised, the whole computer must be removed from the network and totally reimaged and tested. There should be a foolproof and compliant process in place and followed. If you wish to find out more about your options in creating an industry standard set of processes here, you can speak with Fort Safe.
Recover
For this function, the question to ask is “How do we get things back to normal?” Data could be lost and need recovery. Machines have to be put back online, but only after making sure it’s safe. If downtime is unacceptable, there will have to be failover systems that can come up immediately (Disaster Recovery and a Business Continuity Plan). Communication is as important as technical fixes when the object is to get everything running again with minimal loss of time. If the response has been on-point, then recovery should be relatively straight forward. In the case of the malware compromised machine, it would be put back into the corporate fleet.
Implementation Tiers
NIST defines four Implementation Tiers or levels of thoroughness in cybersecurity risk management. Their purpose is self-assessment, and where an organisation needs to be depends on what it does – not every organisation needs to be at Tier 4. Those that are at Tier 1, though, unless they’re very small, should really aim for at least the Second Tier.
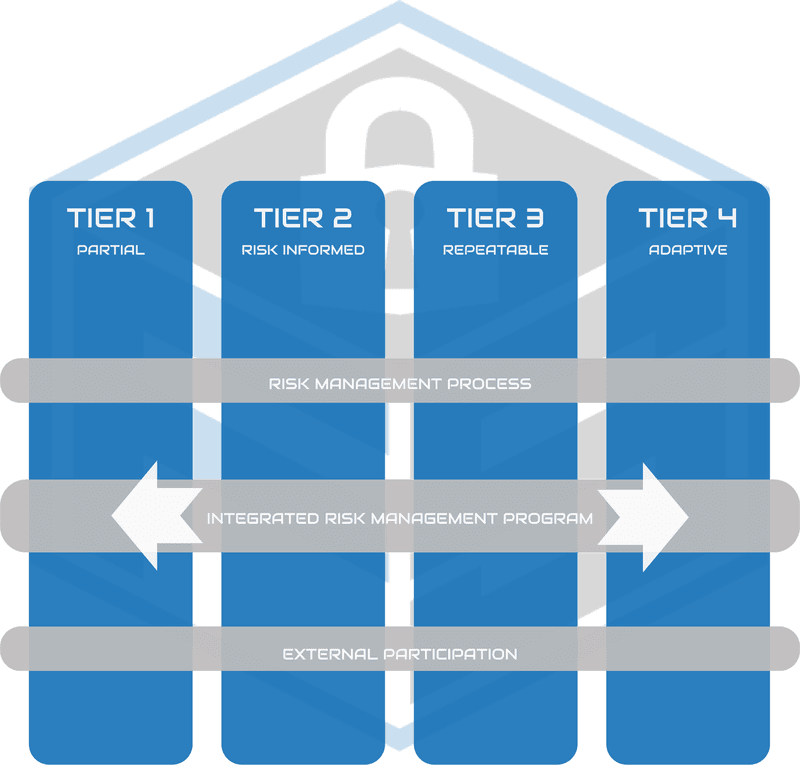
Tier 1: Partial
There isn’t much organisation of cybersecurity risk practices. The IT department could be doing an excellent job with what it has, but awareness doesn’t extend to the organisational level. Their work isn’t coordinated with a systematic risk assessment.
Tier 2: Risk informed
At this level, management is involved in assessing and managing risk. There are processes for maintaining and improving security. However, there’s no organisation-wide policy. Sharing of security-related information happens, but not through a formal system.
Tier 3: Repeatable
An organisation that reaches this level has an overall policy for risk assessment and management. Consistent methods are in place for handling incidents. There are regular reviews of security practices, and the people responsible are well-trained. It collaborates with its partners and shares risk information.
Tier 4: Adaptive
In addition to all the Tier 3 practices, the organisation has constant improvement built into its policies and procedures. Risk management is baked into the organisational culture. It’s always aware of the latest changes in the cybersecurity landscape.
Framework Profiles
The Framework Profile is the informational tool for identifying where an organisation is in cyber risk management, and where it wants to be. It maps the core functions, categories, and subcategories to the business requirements, resources, and risk tolerance. There can be multiple profiles. The current profile will describe how security is currently managed, and the target profile will say where it should be.
Profiles need to take business and regulatory requirements into account. A power plant, a hospital, and a public advocacy group will have very different profiles. In some cases, security is all-important; in others, it has to be weighed against ability to respond to customers or to the public. Specific legal and compliance requirements apply in some cases but not others.
An Ongoing Process
Security is a job which is never finished – there’s always room for improvement. New threats emerge, business networks constantly acquire new equipment and applications, and requirements change. Everyone, large or small, needs to have measures in place to protect against threats and act when issues arise. Many will find the NIST Framework a good way to organise and plan their cybersecurity policies and practices.
If you wish to understand how you can improve your security posture through the adoption of the NIST Framework, reach out to Fort Safe today.