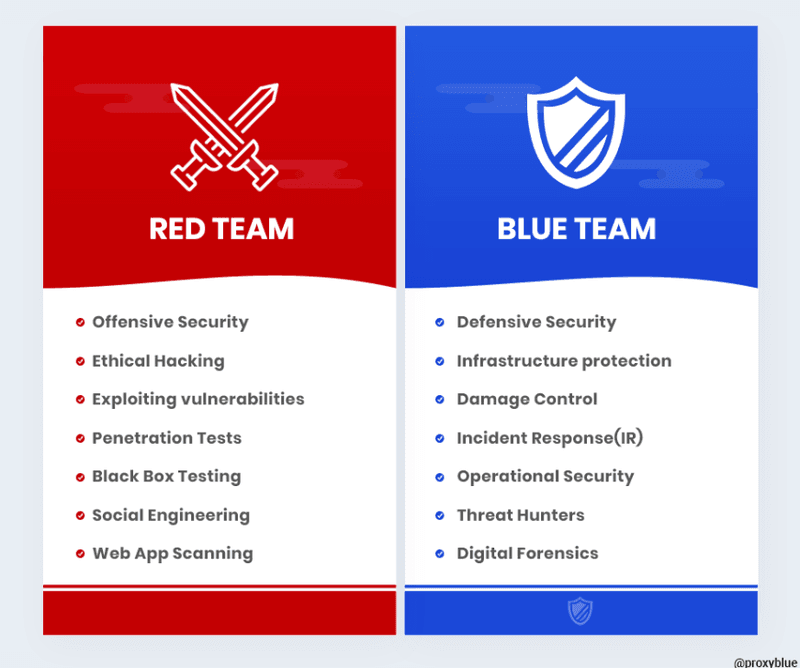
The “blue team” in cybersecurity is the defensive team; the one charged with countering the attacks thrown at a network. The term originates from military wargames with red and blue teams. In cybersecurity, it originally applied to pentesting, where the red team launches authorised attacks and the blue team tries to frustrate them. Usually the red team is an external consultancy, while the blue team is the internal IT security staff, conversant with the ecosystem they’re guarding.
The term has broadened to include cyber defence against genuine black hats. The approach is similar, but with the big difference that real attackers don’t play in a sterile nor predictable series of attacks. Whether the blue team is up against pentesters or real-world attacks, it has to understand and counter that adversary’s thinking. It’s more than just installing firewalls and protective software and hoping they work. The defender’s role is an active one.
Members of the blue team need strong technical skills in system and network management and cybersecurity. Importantly, they need a process-driven mindset focused on operational controls inside the organisation. They also need to be flexible thinkers who can recognise the vectors and newer – even genuinely innovative techniques – and defend against them.
Blue team vs. …
Red Teams
A red team is constrained by predefined rules. It can typically attack only a range of certain, preordained targets. It can’t damage production systems or data, and it can’t actually steal money or other company assets. However, it is allowed to use deception, including psychological tactics and even opsec compromises to achieve its end goal(s).
In a blue team vs red team situation, the driving force is – regardless or organisational mandate – competition. They want to demonstrate capability, and that the red team can’t throw anything at them which they can’t handle. There may not be real-life consequences, but they don’t want to be beaten.
The purpose is to learn. The team will find out what weaknesses its systems have and how it can handle attacks on them. In the end, they’ll patch systems, revise their methodology, tighten configurations, and adopt new tools and operational processes as needed
Black Hats
Cybercriminals are typically seeking access to sensitive data including financial access or records, intellectual property they can use for their own purposes or to sell to potential customers, and of course the opportunity for something analogous to digital vandalism where they may destroy data or even physical assets from harddisks to critical infrastructure like utilities.
When facing real attackers, it’s no longer a game. Genuine threats can try anything they think will work, often without regard to critical (even potentially fatal) implications as can be seen in attacks on hospitals, government departments, and the like. They’re after real assets. If doing permanent damage serves their purpose, they’ll wreck file systems and databases without hesitation, or even for their amusement. They’ll use all the techniques of red teams and aren’t limited in adding any additional tools and techniques to their arsenal.
The blue team’s goal is now survival. The idea of a sterilised capture-the-flag scenario and ‘winning’ are beside the point. Failure leads to lost assets, disgruntled customers, and potentially fines or litigious action. Cybersecurity staff members who fail to protect systems may also lose their job.
Active and Passive Cyber Defence
Blue team best practice requires staying on top of three key aspects;
- Prevention. The cybersecurity team needs to adopt a multilayered strategy to keep attackers out. Techniques include access control, software patching, firewall protection, and anti-malware software.
- Detection. Prevention is never 100% effective. Some attacks get through. The blue team needs to detect intrusions promptly.
- Remediation. Once it has detected a problem, it needs to be fixed as quickly as possible. Damage to data needs undoing. Malware has to be completely removed. The weaknesses that allowed the penetration need to be corrected.
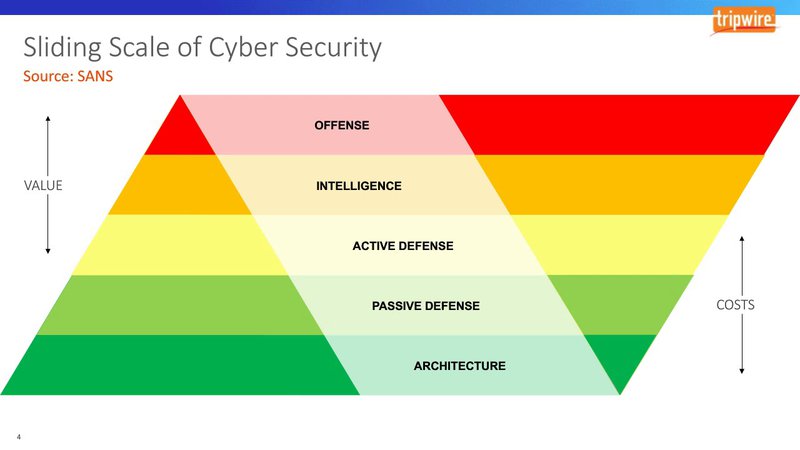
The traditional defensive measures are mostly passive. “Passive” isn’t necessarily pejorative. It means having protections in place that make it hard to penetrate the systems. Firewalls, monitoring, and repair of damage are basically passive. The only problem is that these measures don’t diminish the attacker’s ability to try again.
Adopting a ‘Defense in Depth’ approach where information assurance is held in primacy through the implementation of multiple layers of security controls at multiple levels of the technical and operational ecosystem.It’s about increasing the friction of attackers attempts, slowing them down, allowing for more time to identify and respond.
Active countermeasures try to frustrate the intrusion attempts. They can be as simple as blocking IP addresses and locking out excessive login attempts. More elaborate ones waste intruders’ time while collecting information on their methods through leveraging things like honeypots and canary tokens.
While launching counterattacks is possible, even if under legislative controls where it’s legally permissible, it’s ill-advised as reliable attribution is a fundamentally difficult task. An intruder could be using a hijacked system, and the counterattack might bring down a legitimate but infected server, or there have been deliberate measures to shift the accountability. If the attack is coming from a large botnet, striking back won’t do anything significant to the botnet, but the collateral damage could make the defenders act criminally.
Detecting Probes and Attacks
The best time to catch an intrusion attempt is before it can succeed. Logs give records of failed logins, port scans, and the like. Pulling the relevant information from a mountain of log files may seem daunting, but sophisticated log analysis tools are available. They’ll pull out important trends and show them in graphical form. Intuition plays a role too.
Monitoring is another valuable tool, but only if the cybersecurity team has followed best practice. A sophisticated Intrusion Detection Systems (IDS) covering both network ID’s and Endpoint Detection and Response (EDR), coupled with continuous monitoring by a Security Operations Centre (SOC) gives vital warning to potential attacks. These services, conducted either internally or by a third party Managed Security Service Provider (MSPO/MSSP), should be using a follow-the-sun methodology to ensure reliable coverage. This continuous monitoring should also extend to key assets like web servers or even IoT (Internet of Things) devices that present critical services like financial systems (netbanking) or medical devices.
It’s important that the analysts are well trained in screening and identifying legitimate threats from false-positives. The white noise of normal traffic setting off alerts, can be easily confused with more nefarious probes bouncing ‘harmlessly’, that are gathering information to assist a later attack. These seemingly innocuous triggers can also be a smokescreen for a more serious attempt; misdirection is a favourite technique for overwhelming and getting past defences.
Detecting Intrusions
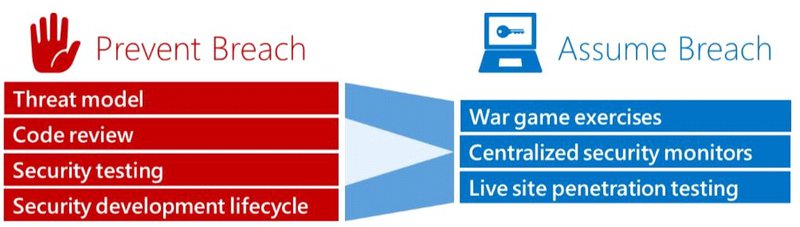
No matter how good the preventive measures are, they cannot be 100% effective. Some intrusion attempts will get through. Three steps are vital in dealing with them.
- Detect and remove them quickly. The faster they’re found, the less damage they can do. The best monitoring and intrusion detection tools don’t just look for malware signatures. They identify behavioural patterns such as abnormal packets and excessive outbound data transfers. This approach catches even zero-day exploits.
- Limit the damage they can do. Network segmentation, role-based authorisation, and encryption are parts of setting up a network so that intrusions can’t easily spread and collect valuable data. When malware is discovered, the infected system needs to be quarantined promptly. Good backups aid in restoring damaged data.
- Make sure the problem is really gone. Obvious attack are often little more than a cover for a more persistent threat. Removing one threat and assuming the problem is gone could let a serious breach hang around for months.
The methods of attack constantly change. “Fighting the last war” never leads to victory.
Remediation and Beyond
Finding and fixing an intrusion isn’t the whole story. The next step is to find out what it missed and what underlying weaknesses made it possible.
If an account is compromised and isn’t fixed, removing the malware accomplishes little. An unpatched vulnerability likewise remains open for further exploits. A downloader or backdoor could remain in hiding, ready to restore malware which is removed. Real remediation requires discovering the underlying problems and correcting them.
A defensive team that only treats symptoms is missing the point. Misdirection is at the heart of both red teaming tests and criminal intrusions. If they can get the blue team to think the problem is solved when it isn’t, they’ve won. An intelligent incident response team – and ideally precogitated incident response strategy – conducted by a team like Fort Safe can improve the security posture of any organisation. As vulnerabilities may reside in people rather than technology, through social engineering techniques, they too must be addressed. If employees are fooled too easily, no technical countermeasures will make up for it. Blue team members need to understand human and operational challenges as well as technical ones.
Defence by Deception
Direct counterattacks are far too perilous from a business and legal standpoint, but deceiving would-be online intruders is fine. Just as misdirection is a major tool for the attacker, it’s an excellent one for the defender. Too.
Deceptive techniques include honeypots and honeynets. They look like valuable targets, but they contain nothing of importance. Fake vulnerabilities which aren’t really exploitable are another variation. The idea is to let probes discover them first and try to exploit them, while defenders gather information about the methodologies of their attempts. From picking up IP addresses to block, to the intelligence gathered in the discovery of techniques used can improve the real defences against them.
Success with the Blue Team
Whether it’s defending against pen testers or real aggressors, blue team best practice means a proactive approach to cyber defence. Its members need strong cybersecurity skills and sharp minds. Setting up firewalls and anti-malware software is important, but it’s not enough. The defenders need to understand their adversary’s thinking. It’s not just a battle of software; it’s a battle of human minds. The blue team needs to be just as devious in its thinking as its opponent in order to win, and just as determined.
If you’d like to understand the state of you current blue team defensive strategy or wish to discuss the implementation of one to increase your security, reach out to Fort Safe. Fort Safe provide assistance with reviewing and developing your technology landscape and procedures.